Allowing or denying permissions to a user or group is controlled by access token. I have already discussed the general method of granting permissions in windows 8. Before going through the steps let me throw some light on the access token. Access token encapsulates a security descriptor which contains information on security for a particular user or a group and describes the security related issues of a process.
A security descriptor has a security database called authentication database where it has all information on login sessions and other security credentials stored in it and hence it has the ability to identify the owner of a process by comparing the password and username entered, with that stored in the database. If the credentials match, they are considered to be authentic and an access token is created by logon service against each match. So every files created, every process executed and each and every functions performed by that user has a copy of that token. So when a process which is access controlled has to run, Windows asks the security descriptor if the user owning the process is permitted to access the object or in case it is allowed to access what type of function it can perform, only readable, only writable or both? If the process is not permitted to access the desired information, the request is denied or else the process proceeds further.
There are generally two types of tokens-primary and impersonation token. So these access token are responsible for allowing and denying permissions of access to a user or a group. The customization of access is done by the Administrator or to be more transparent, Administrator decides which user or group can access what data, from which folder or drives and if it does what type of function can the user perform on that particular data. The following tutorial tells you how to do this using command prompt. The commands used are generally known as pipe commands. The following table shows some frequently used permission parameters and their corresponding switches. However there are many more parameters which can be found very easily in the elevated command itself. For that just open the elevated command prompt and type the following command icacls /? and press Enter. You will get all the pipe commands.
| SWITCH | PERMISSION |
|---|---|
| N | Deny all access |
| F | Allow full access |
| RX | Read and Execute Access |
| R | Read Only Access |
| W | Write Only access |
| D | Remove user or Group for No Acess |
Steps to Allow or Deny Access Permissions to Users and Groups in Windows 8 from Command prompt
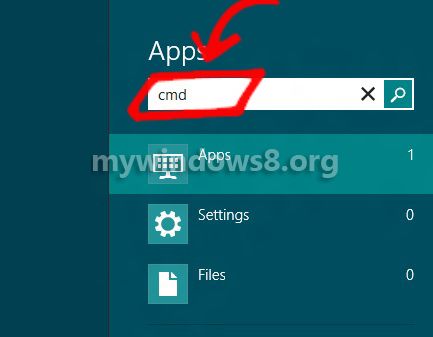
1. First of all open the elevated command prompt i.e. press Windows + C to open the Charms Bar-> Search->Type cmd in the search field.
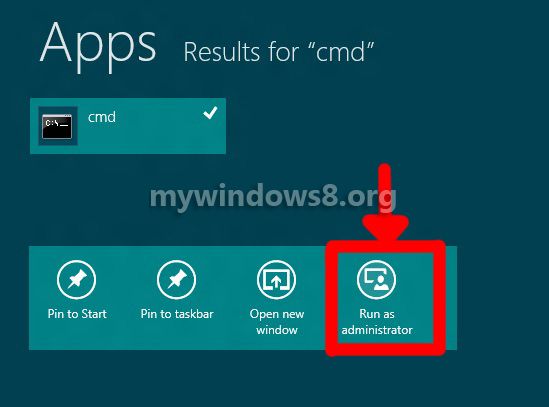
2. Now right click on the result, and see that at the bottom of the screen there is an option called “Run As Administrator”. Click on it. If prompted by User Account Control, hit Yes to confirm. The image below will show how to open the elevated command prompt. Although the options appear at the bottom of the screen but here I edited to bring to closer to the search result for reason of size restrictions.
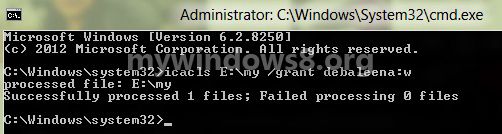
3. So your elevated command prompt is opened. Now to access or deny permissions for a file, type the following command icacls “full path of file” /grant “user name or group”:switch and press Enter.
“full path of file” means the path of the file for which you want to put access or deny permissions, the User account means the name of the user containing the file or drive and switch letter denotes the type of restriction to be imposed. Close the Command prompt after use.
The following table shows the Switch and the related permissions

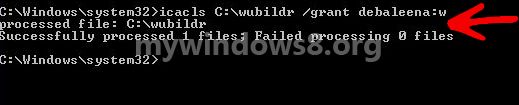
4. Or if you want to allow or deny access to a folder or a drive, repeat steps 1-3 and type the following command icacls “full path of folder or drive” /grant “user name or group”:switch /T and press Enter. Close the command prompt after use.


How do you do this without using the useless and counter-productive “charms” ? I am trying to gain control over every file in the computer, taking it away from microstupid who created this garbage O/S that I was talked into… I want to be able to change, delete, modify and/all files on the computer, just like I used to be able tyo, and I also want to deny that ability to microstupid… I want to disconnect their “cloud”, not be required to use a microstupid account for anything, get rid of their braindead ‘apps’ and the winslow schlockstore, and regain control over MY computer. I don’t like them reserving control over hundreds of settings, forcing me to use bong or internet destroyer for anything… suggestions ?
Dude!! you are really frustrated with Windows 8.. Please tell your issues one by one.. we will be happy to help you.