PPTP means point-to-point tunneling protocol. It was introduced in 1995 as a VPN protocol. PPTP was released about a decade after its invention. Prior to PPTP, PPP was the VPN standard. PPP did not have a tunneling feature. PPTP began as a protocol that was implemented on Windows systems. In quick order, it became the go-to protocol for a number of platforms.
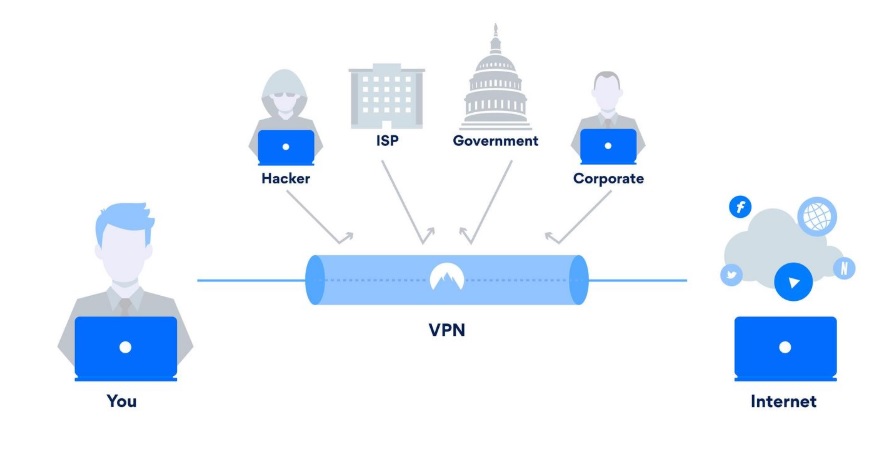
Although PPTP protocol is offered on just about every VPN service, it is not secure. The following are a few of the reasons why.
PPTP Is an Obsolete Protocol
PPTP dates back to Windows 95. This security protocol has not been updated as frequently as newer protocols have that use strong encryption. This is why free VPN services or very cheap VPN services will offer PPTP protocol. It’s old, so doesn’t cost them anything. Most free VPNs are not concerned about keeping the client’s information secure. Their goal is to make money off of the client’s data. When a VPN solely relies on PPTP protocol, their client’s data is at risk of getting leaked.
Some might counter that PPTP is fast. And that’s true. A VPN that solely uses PPTP is not going to slow down your Internet traffic like other protocols, such as OpenVPN. But that’s because PPTP doesn’t have strong encryption, so it is not going to slow down your Internet speed.
The first flaws found in PPTP’s cryptography surfaced in 1998. By 2012, so many vulnerabilities surfaced that PPTP could be broken easily using a number of tools that were readily available on the market. One expert says about PPTP that the only person who cares about using it are those who do not care about the communications they are trying to protect. Some of the flaws that were found include:
• The possibility of decrypted data being sent through the protocol
• Password theft vulnerability
• Vulnerability for MITM attacks
If PPTP Is so Insecure, Why Is It Still Being Used?
There are two reasons why PPTP is still in use.
• One reason is that it has come pre-installed on a number of operating systems for a long time. It’s tradition.
• The second reason is that it’s easy to get going. You do not need to install anything.
How Does PPTP Compare to Other Protocols?
PPTP vs. L2TP/IPSec
As you might have guessed, L2TP/IPSec is better than PPTP. Some of the features that make L2TP/IPSec superior include:
• The ability to be used with 256 bit encryption keys
• It can use the AES cipher
• It can be configured so that NAT firewalls cannot block it
PPTP can easily be blocked by firewalls. The only thing that PPTP has over L2TP/IPSec is the online speed it offers. PPTP might be a good idea if you need faster speed and want the ability to get around geo blocked content. But it doesn’t always work.
PPTP vs. IPSec
PPTP and IPSec share some similarities. For example, they both use encapsulation technologies. However, IPSec is a whole lot more secure. PPTP is a lot more stable than IPsec. However, PPTP is a lot easier to block with the firewall. IPSec has the ability to encrypt traffic in a way that the end application is not aware of the encryption. So PPTP is faster than IPSec and a lot easier for the VPN provider to configure.
PPTP Versus OpenVPN
When it comes to security, OpenVPN takes the cake. This protocol is able to use the AES 256 cipher. It can use any port. OpenVPN is open source. This means that people more readily trust it than they do Microsoft, the team behind PPTP. Microsoft is already known to cooperate with the NSA.
It is difficult to block OpenVPN traffic because it’s difficult to distinguish it from SSL or HTTPS traffic. OpenVPN protocol can be found on a number of respected VPN services, including NordVPN.
Of course, PPTP does better on speed than OpenVPN. There is the option to use OpenVPN on UDP to improve the speed, but it’s nothing close to what you get with PPTP connections. Also, configuring PPTP is a breeze compared OpenVPN. OpenVPN can take the better part of a day to configure, depending on how experienced you are with it.
Can You Make PPTP Safer?
Kind of, but not really. MSCHAPv1 was Microsoft’s first attempt to make PPTP safer. More than a decade and a half ago, this encryption was broken. It was replaced by MSCHAPv2, and this has been shown to be weak almost since its inception. You can easily brute force attack it in a few hours. There are even online services that can break it.
You might ask about EAP – TLS authentication. Yes. This can make PPTP more secure, but it needs a full public key infrastructure. Most people who are not planning on building an enterprise VPN do not have the time or energy to dedicate to something like this. PPTP is thoroughly broken. Anyone who says otherwise is probably trying to sell you something.
Should I Ever Use PPTP?
Most VPN services are going to give you a choice of VPN protocols. Before choosing PPTP, you need to ask yourself a few questions:
• What are you intending to use the VPN for?
• Are you willing to trade security for speed?
• What devices will you be connecting from?
PPTP should be viewed as extremely vulnerable. It’s not the right choice for anything that requires high security. There are too many better options available.
PPTP should only be used when you are using a VPN because you want to hide your location and want to access the Internet with speed. PPTP could be good for unblocking geo restricted websites or streaming videos from Netflix or YouTube.
Even this could be problematic if you are concerned about somebody snooping in on your Netflix or YouTube viewing habits. Use PPTP with caution and at your own risk.
We would love to hear from you. Do you still use PPTP as a VPN protocol? If so, why? Let us know what you think in the comments section below.

