The number of unsuccessful sign-in attempts that will result in a local account being locked is determined by the Account lockout threshold policy option. Until an administrator unlocks it or the number of minutes specified by the Account lockout duration policy setting has passed, a locked account cannot be used. You can specify that the account will never be locked by setting the number to 0, or you can choose a value between 1 and 999 failed sign-in attempts. Account lockout duration must be greater than or equal to the value of Reset account lockout counter after if Account lockout threshold is set to a value other than zero.
Automated brute force password attempts can be made on any or all user accounts, testing tens of thousands or even millions of password combinations. The effectiveness of such attacks can be almost completely eliminated by limiting the number of attempted failed sign-ins. However, it is significant to remember that a domain with an account lockout threshold configured could be the target of a denial-of-service (DoS) attack. A hostile individual might automate a series of password attacks against each and every user in the company. The attacker might lock all accounts if the quantity of attempts exceeds the threshold value for account lockout.
This guide will teach you how to modify the Account lockout threshold so that a local account is locked out of Windows 10 after a predetermined number of unsuccessful sign-in attempts.
To modify the Account lockout threshold, you must be logged in as an administrator.
To change account lockout threshold for local accounts using command prompt
1. Launch a command prompt from a higher level.
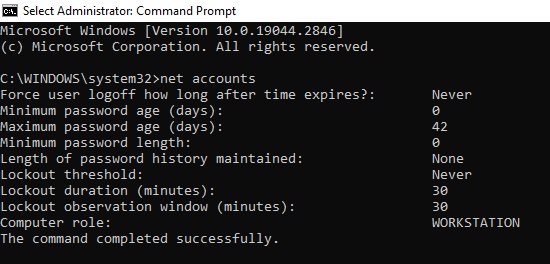
2. Type the command shown below into the elevated command prompt, and make note of the current Lockout threshold.
net accounts
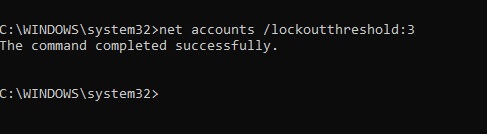
3. Enter the command below into the elevated command prompt, and press Enter. (see screenshot below)
net accounts /lockoutthreshold:Number
Note
In the command above, replace value with a value between 0 (none) and 999 to indicate how many failed sign-in attempts you wish to allow before the account is locked out.
For local accounts to never be locked out, the default value is zero invalid sign-in attempts.
4. If you’d like, you can now close the elevated command prompt.
5. Instead of the default 30 minutes, you can customize the Account lockout length and Reset account lockout counter after policies to anything you like.

