Before going to the steps, let’s know in brief about security descriptors in Windows. A security descriptor is a structure and its associated data that contains the security information for a securable object. The main function of a security descriptor is to identify the object’s owner and its primary group. The role of a security descriptor is not limited to identifying owner or primary group, but also to manage DACL. DACL and SACL are parts of ACL (Access Control List). Access control list is a complete list of Access control entries. Each ACE in an ACL identifies a trustee and specifies the access rights allowed, denied, or audited for that trustee.
An ACL can be classified into DACL and SACL.
DACL or Discretionary Access Control list checks and identifies if a trustee is to be allowed or denied access to a securable object. When a process tries to access a securable object, DACL tracks the system and check if the process is enlisted to get access. A DACL is very important because without it, any process an access any object which is derogatory to the security of a system.
SACL or System Access Control List: A system access control list (SACL) enables administrators to log attempts to access a secured object. In other words, when a process tries to access a securable object, SACL records the type of attempts that the trustee process made in order to access the object.
The security descriptors of the user and the associated configured value of the system need to mach with each other in order to provide the user access to the desired object.
Now this access of logs can be managed by the Administrator of the operating system from the Local Group Policy Editor. The policy setting which is used for the purpose specifies the security descriptor to use for the log using the Security Descriptor Definition Language (SDDL) string. If you enable this policy setting, only users whose security descriptor matches the configured value can access the log. If you disable this policy setting, only system software and administrators can write or clear this log, and any authenticated user can read events from it.
If you do not configure this policy setting, the previous policy setting configuration remains in effect.
Steps To Configure Log Access (Legacy) in Windows 10
1. Press Win+R to open Run window.
2. Type gpedit.msc and hit Enter to open the Local Group policy Editor.
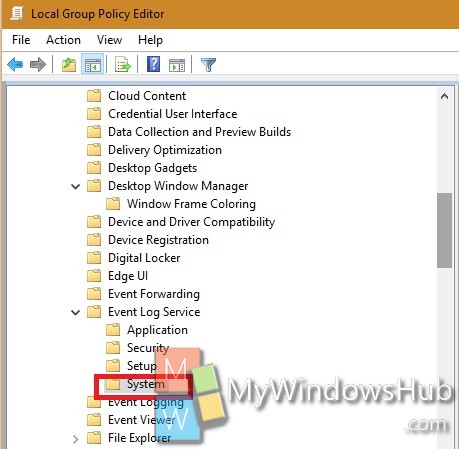
3. Now go to the following location Computer Configuration > Administrative Templates > Windows Components> Event Log Service> System.
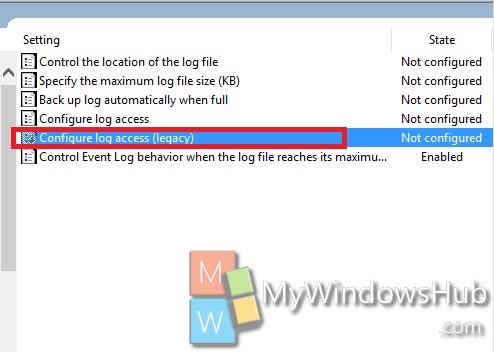
4. In the right panel, you will find the policy setting Configure Log Access (Legacy). Double tap on it to edit the policy.
5. If you want to enable log access, then check Enable. Go to Step 7.
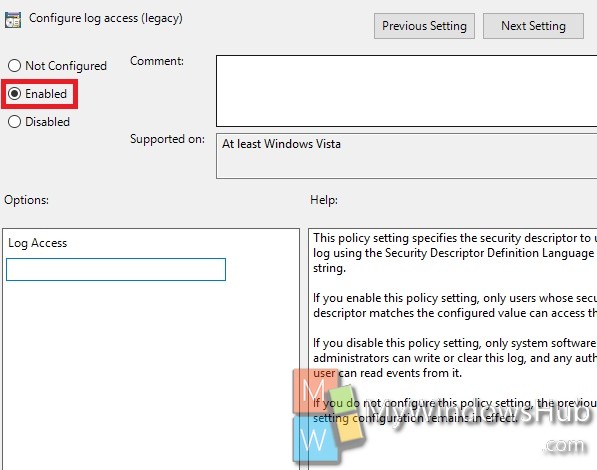
6. If you want to disable the option, click on Disable.
7. Click OK and then Apply.
8. Close Local Group Policy Editor.


Mejoras en Windows